How I sent multiple payment requests on PhonePe, Paytm, and Google Pay 🤑💰
Good day ppl! This is Anudeep Vysyaraju, with a new write-up on how I sent multiple payment requests to users on their PhonePe, Paytm, and Google Pay.
Also, I’m coming up with more interesting writeups, and let’s hack together!! 👨💻🧑💻
Let's get started…

Few lines about Razorpay!!
Razorpay helps you accept online payments from customers across Desktop, Mobile web, Android & iOS. Additionally, by using Razorpay Payment Links, you can collect payments across multiple channels like SMS, Email, WhatsApp, Chatbots & Messenger.
Let’s re-create the scenario!!
I just want to prank 😅 my friends in a new way, So I’m thinking and searching for some alternative ways to prank them 😂😂 and I got an idea for Rate-Limiting vulnerability, If I use any routine things such as OTPs, etc it won’t be much interesting 😂😅 and they just ignore those messages.
So I found an alternative way for Rate-Limiting just to prank my friends 😂
This is how my hunt started on this website for vulnerabilities😈😈
Let’s move into the hack!!!!
I started searching 🔍 for a website that has a Rate-Limiting vulnerability and found nothing. After some time I got an idea and just wanted to check whether it's possible or not on a website, So quickly I fired up the burp and started intercepting the requests on a shopping site but found nothing, Now I observed that the website is using Razorpay gateway and sent some of the requests to my Repeater that look somewhat special to me 😉😉
After searching 🔎🔎 all the requests, I saw a request that takes all “MY EYES” 👀👀👀 towards it…..

In this request, we can observe some parameters such as UPI ID, Description, Amount, etc.
After seeing the request, I came to know this is the request that user receives as a Payment request on their UPI Application 🙂
Now I’m thinking 🤔🤔 about how I should use this request and what to do with it, also I tried multiple things on it but no use….. 🤷♂️🤷♂️
Nearly been 15 minutes, by mistake I forwarded this request to the repeater in Burpsuite then I was able to see the Payment Request on my phone!! so this means the payment link or request is still active 😅
I literally thought this was my only HOPE to get something 😁😁
Now immediately, I sent the same request to the Intruder in Burpsuite, and want to check 😈😈 after sending the request to the Intruder it looks like this….
Also clear or remove all selections to make the request more clear.

Now select the attack type as Sniper and go to the Payloads tab, Here select the payloads type as “Null payloads”.
For Null payloads, it’ll ask how many payloads to generate and give your desired value. I’m giving as “100" for testing purposes you can give as you desire to tease your friends 😂😂😂😂😂
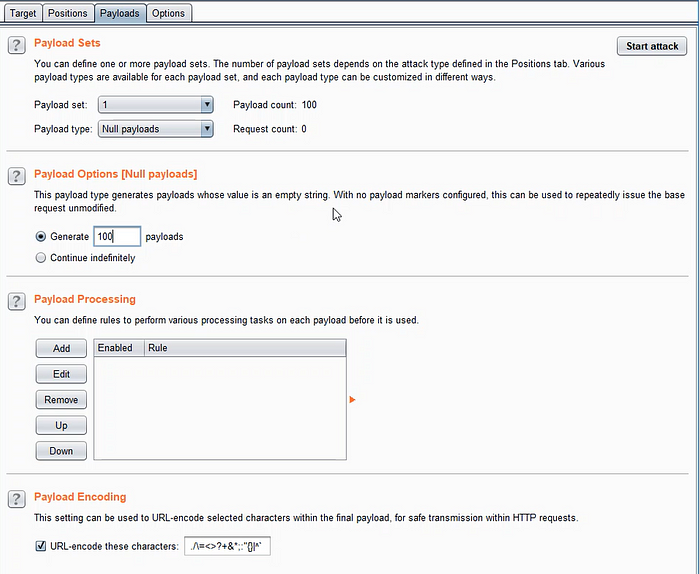
Now you can see the button called “Start Attack”, tap on it. >>>>>>>
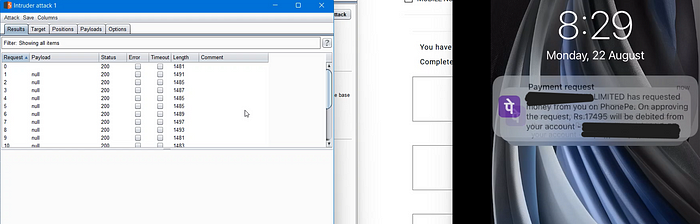
Booommmmmmmm😈😈 now you can see that payment requests are sent to the given UPI ID 😂🤣😂🤣
Similarly, you can give the UPI ID of Paytm, Google Pay, etc on Razorpay Payment Gateway to flood the Application. 😂😂
PS: Just shared this write-up for Knowledge Purposes. So please be aware while exploiting it. Also, the bug has already been submitted to Razorpay via the HackerOne Platform and they marked it as Informational.
Also special thanks to Mayur Parmar, Hemant Patidar, Tarun Tandon, and Pavan Kumar Chinta
Hope you enjoyed this write-up and gained something good. Visit my profile for doubts and guidance ping me on LinkedIn.
Also, you guys can follow me on Medium
Thanks and Byee… Happy hacking and Let’s hack together👨💻😈
